Some Insights and Numbers on Cyber Risk
This piece will briefly discuss the most common types of cyber insurance losses, their likelihoods and loss costs .
We’ll leave industrial process and control system cyber risk out of the discussion, as it is not insured under customary commercial cyber insurance.
Let’s begin with the basic types of losses.
Types of Cyber Events
There are four basic types of cyber loss events. All events can be covered by cyber insurance.
Ransomware or Malware: a virus or malware is embedded on a server that encrypts the data on that server and/or prevents the server from working. Nothing is stolen but a ransom is demanded by the perpetrator for the decryption key. This is the most common type of cyber loss. Less frequently, malware will shut down a server without ransom and even maliciously manipulate data.
Denial of Services or DOS: servers are bombarded/saturated with incoming requests from the internet, overwhelming communication and the web servers.
Business Email Compromise (including “social engineering”): a phony invoice is submitted from an imposter email address and paid. A CFO or other senior officer is scammed by imposter email into authorizing a fund transfer to the imposter’s bank account. Alternatively, by clicking on a link in an email, the user is tricked into revealing data.
Data Breaches: unauthorized entry (hacking) into a database and theft of its information. For instance, a flash drive or laptop is stolen and the information stored on it is exposed. Liability may result for compromise of Personal Identifiable Information (PII) may result particularly from payments cards (PCI). For health care firms, breach of Personal Health Information (PHI) may also result.
For all four types of cyber losses, extra expense can be incurred in the form of ransom, investigation costs, consulting advice, notification costs and credit monitoring costs. Occasionally, there are also legal fees and fines.
Cyber Event Impact
The typical severity of each type of event is now discussed. All values are in USD, except where indicated.
Ransomware: these events may not be particularly severe to an organization if data and emails are backed up. Ransom amounts have increased significantly over the years, now averaging close to $5 million according to the Ponemon Report Data. Discovery and recovery times average almost 300 days involving technical work in reloading servers and rebooting email accounts. If crisis management services are used, these costs could be significant.
Denial of Services: these attacks inundate with emails and sign-ins, paralyzing a website, and can cost companies lost revenue, mitigation, and reputational damage. Large-scale attacks on major enterprises can result in millions in total losses, with some exceeding $1.5 million per incident. The financial toll varies by industry, with e-commerce, finance, and tech firms being prime targets for costly disruptions.
Business Email Compromise: depending on the size of the target and the sophistication of the scheme, the average cost of a fraud loss from business email compromise is about $150,000. However, very sophisticated scams on large companies can be much much larger. There are several such rare but extreme outlier BEC scams. In 2016, a European manufacturer (Leoni) was swindled out of €40 million by one email. Ubiquity Networks lost $47 million in a single wire transfer scam. Outliers aside, the MFL for social engineering fraud for most firms depends upon the firm’s internal controls on large wire transfers or cheques. Successful social engineering scams are becoming less frequent as awareness of them increases.
Data Breaches: most often perpetrated on firms with PII (Personal Identifiable Information), PHI (Personal Health Information), and PCI (Payment Card Information). Expected loss costs from data breaches are much larger than from the ransom and BEC events. Substantial loss data on data breach loss costs is available, making quantum assessment of data breaches easier.
Data Breach Loss Data: Ponemon
A widely quoted source of cyber security breaches and data breach losses is the Ponemon Institute’s Cost of Data Breach Study. Here are a few observations that might provide useful perspective:
Ponemon looked at some 604 data breaches, each of between 2,100 and 113,000 lost or stolen records.
The average breach involved about 26,000 records and had an average loss cost of about $5 million. Law enforcement involvement decreased the average costs of a breach by about $1 million.
The average cost per lost or stolen record was about $175. (This unit cost was recorded by Ponemon in 2019 at $150).
The unit record cost varies from breach to breach, but according to Ponemon is not significantly affected by the size of the breach (i.e. whether its 5,000 or 100,000 records).
The average time for discovery of a data breach was just over 7 months.
The breakdown of Ponemon data breach costs is roughly as follows:
Post incident costs include consulting fees, defence costs, legal liability and identity protection and credit monitoring services to victims. The business loss aspects were estimated indirectly using “churn rate statistics”. For instance for financial institutions, Ponemon reported that the churn rate (i.e. the customer attrition rate) was about 4% higher on average after a data breach.
Interestingly, the Ponemon data reveals that data breaches that used external consultants had higher costs than those without, i.e. external assistance did not appear to be cost-effective.
Liability for Data Breach
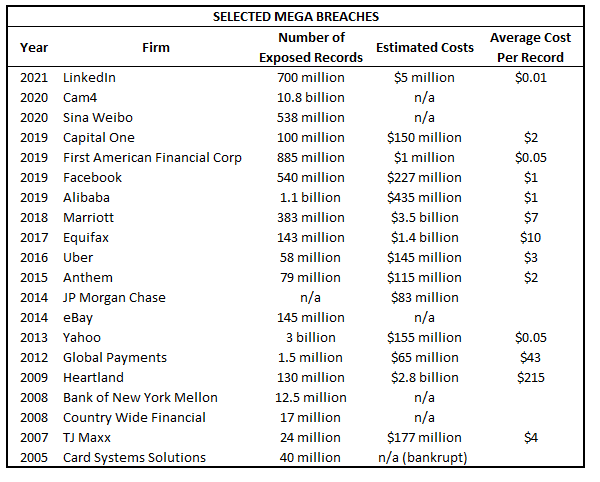
There have only been a handful of recorded “mega breaches” (>1 million exposed records). Here are a few:
In the US, the majority of courts have dismissed suits for negligent releases of information unless the plaintiff can prove actual damages. There are exceptions to this, for instance a 2004 case involving Choicepoint and 163,000 exposed records, for which liability of about $60 per record was found even though there was no identity theft. In the 2009 Heartland case (130 million records), $110 million in liability to banks and credit card companies was imposed upon Heartland, but no liability to individuals. In 2016, Uber tried to cover up a data breach. In 2018 they agreed to a $148 million settlement.
However, if identity theft is established and actual damages are proven, liability for data breach is nevertheless imposed in the US.
In Canada, there are a number of data breach cases where claims have been made and, in a few cases, litigated.
At the end of 2019, a class action lawsuit was filed against LifeLabs, who had a data breach of 15 million Canadian patients. Compensation has been requested at $1.13 billion CAD.
In 2017, Equifax had a data breach that affected 19,000 Canadians. A $300 million fund was established to compensate those affected in the US. This figure does not compensate Equifax’s Canadian customers.
A 2011 $40 million CAD class action suit against Durham Regional Health settled for $500,000 CAD plus allowance for more payments to individuals who could prove actual financial loss.
In a 2014 decision involving the Bank of Nova Scotia (Evans), a class action against the Bank was certified arising out of a release of 643 customers’ information (138 of whom had actually become identity theft victims). Costs were not released but have been estimated by some at less than $1 million CAD.
Other Canadian class actions include:
Condon v. HRSD Canada (2014): 583,000 student loan files
Hopkins v. Kay (2014): 280 patient records (based solely on the tort of “intrusion upon seclusion”; no actual identity theft apparently)
Wong v. TJ Maxx (2006): settled for costs of credit monitoring, identity theft insurance and $30-60 for each class member
Speevak v. CIBC (2005): reportedly settled for less than $150,000
Jackson v. Canada (Correctional Services): release of 360 employee records; reportedly settled at about $500,000
IIROC: release of information on 52,000 investment clients on which $52 million in damages ($1,000 per client) is sought. Thus far IIROC has spent $5.2 million. No fraud or identity theft has been reported, but the case is ongoing.
Obviously the IIROC case stands out as the MFL, at somewhere between $5 million (incurred) and $50 million (reserved).
Note that, unlike US courts, some Canadian courts appear willing in some instances to award for liability where no actual financial loss has occurred under the tort of intrusion upon seclusion (maximum $20,000 per person), presumably for psychological and aggravated damages. However, other Canadian courts have declined to award these damages for what they term “mild disruption”.
Takeaways on Cyber Liability
An organization that suffers a data breach would be liable for any actual fraudulent use of released records and costs to third persons directly associated therewith.
That said, significant liability is only seen for release of PII, PHI and PCI records.
If your firm doesn’t handle these, cyber liability risk is nominal.
Liability for release of other records (e.g. addresses, phone numbers, invoices, accounting records, etc.) in the absence of any fraudulent use of them may still be imposed in Canada (intrusion upon seclusion). Again, liability is likely to be nominal.
Event Likelihoods
The likelihood that any given organization will actually suffer one of the three types of cyber losses is, of course, of uncertain probability.
Loss data indicates, that probability will depend primarily upon the following factors:
size of organization
business sector
amount and nature of personal identifiable information (if any)
cyber security controls (firewalls, procedures, internal controls, ani-virus software, training)
However, even rough estimates of individual likelihoods are difficult from the loss data. From research and reading, the likelihoods for most firms (other than financial or health care) seem to be in one in 50-100 year probability ranges (note these are not likelihoods of attack, but the likelihood of a successful attack).
What Does It All Mean?
Risk assessment is speculative and can be misleading if you miss a “black swan”.
For any firm that does not keep PII, PHI or PCI data, the MFLs are likely less than $1 million. For a firm with these data, the MFL is based on a maximum foreseeable data breach. This MFL could serve well as a cyber liability insurance limit.